h8mail🤖: How I found all your 😈 Hacked Google Passwords ☠️
- alvin gitonga
- Apr 30, 2023
- 3 min read
Updated: Jul 5, 2023
CyberMorans🤗

There are a many places where compromised emails and passwords ☠ are stored and not all of them contain all the latest dumps😝 But there is a tool that can search through all of these databases and determine whether an email has been compromised 😈 and which data dump compromised it!.....very convenient😋

h8mail is a tool for finding compromised email addresses and their passwords😈 from these data breaches💀. When you combine this tool with others such as TheHarvester or the crosslinked tool, you can harvest email addresses from an organization you wish to target and then test to see if they have been compromised...Then use the credentials to gain initial access on the Organization. Although there are numerous tools to do so, h8mail may just be the best!😎

In this Post, I showcase how to use h8mail to quickly and effectively find an email😎 in these data dump databases that may contain a current password or hash of the password😵💪

🚀 Install h8mail
The first step If you have not yet installed pip3, you can do so by entering👇
kali > apt install python3-pipWe can simply download it from pip3👇
kali > pip3 install h8mail🚀 h8mail help
Before get started, let's look at this tool's help screen. When I installed it, the package placed my binary file in /home/kali/.local/bin. Yours may be different. If this directory is not in your $PATH variable, you will need to add it or simply navigate to the directory where the binary is located👇
kali > cd /home/kali/.local/binNow, preface the command with the name of the interpreter (python3), you should be able to run this script. Simply append a -h after the command to display the help👇
kali > python3 h8mail -h
h8mail has muchas muchas opciones😝 -- but in its simplest usage, the syntax looks something like this👇
python3 h8mail -t <target email address>🚀 Add the API Keys
Next, we need to create a configuration file and provide API keys to the databases we want to search. Create a config file👇
kali >python3 h8mail -gh8mail will now create config file in the directory you executed this command from. I ran the command from /home/kali/.local/bin, so my config file was placed in that directory. Yours may be different, but h8mail will display the directory and file name after creating the file like so👇

Now, you have the option to use API keys from the premium services such as haveibeenpwned.com. To do so, click on the API tab at the top of the screen 👌
haveibeenpwned.com is among the largest repositories of data dumps on the web. They require that you first provide a password and verify it. Finally, they ask that you pay a nominal $3.50/month to use their service....👇

Once you have an API key, open the config file and place the API key in the config file 👇
kali> mousepad /home/kali/.local/bin/h8mail_config.ini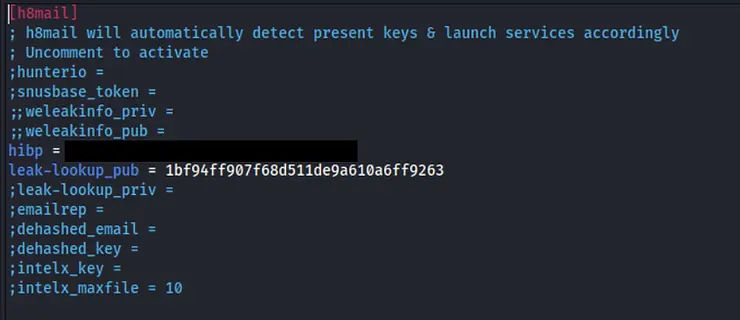
Place the API key after the hibp (haveibeenpwned) or the respective service line and uncomment it and the 'leak-lookup_pub line', incase you have used haveibeenpwned as well...✊
Now lets HUNT! 💪

🚀 Searching for emails in dumps
h8mail's syntax is rather simple😁. We only need to use the -t option followed by the target email address or a text file with a bunch of emails to search the dumps for the email(s) followed by the -c option and the location of your config file, such as👇
kali > python3 ./h8mail -t emails.txt -c /home/kali/.local/bin/h8mail_config.iniHit enter and h8mail begins its search through the databases we specified in the config file👇

If we want to save the results in a text file, we can use the -o option followed the name of file we want the results saved to 👇
kali > python3 ./h8mail -t emails.txt -c /home/kali/.local/bin/h8mail_config.ini -o PostaKiserian_results.txtTo open the output file, you can use any text editor or the less command to view the output. to do a search of a specific email we only have to use the h8mail -t argument like 👇
kali > python3 ./h8mail -t tom@myspace.com
🚀Conclusion 🤖
Subscribe to receive notifications of similar posts 😜 where we will be reverse engineering malware, vulnerabilities as well as hacking tools, vectors, stories, tutorials and other Infosec stuff...😋
Follow me on twitter for daily Infosec Memes and shenanigans😝
Morans,

Thank you for taking time and hope you learned something new, Like/Share and leave a comment/review and as always, stay awesome! 😋👊 💪






Comments