Spying🤫and Hacking😈 Bluetooth devices
- alvin gitonga
- Jun 25, 2023
- 4 min read
CyberMorans🤗

Bluetooth hacking offers attackers😈 a window of opportunity to access confidential information on phones and tablets🙊. Although Bluetooth shares the same frequency of 2.4 GHz as WiFi, the protocol used here is different. You cannot use the same resources as WiFi Hacking😋
In this post, learn how to identify nearby Bluetooth devices, using purely the built-in kali features and bettercap for locating devices, and target devices😈
Morans, Lets do this then...😋💪

🚀 HCICONFIG
The first tool is hciconfig same as ifconfig but it is for Bluetooth devices. Hciconfig is the tool used to configure Bluetooth devices. See attached Bluetooth devices or can add the Bluetooth devices and configure them 👇
kali > hciconfig
When you open hciconfig the state of the device is DOWN. The device should be in UP and Running state 👇
kali > hciconfig {your-MACaddress} up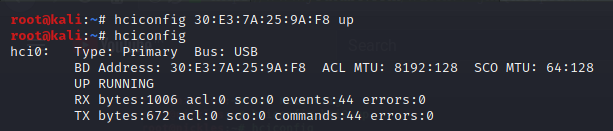
After this command, you can run the hciconfig command again and see that the state has changed to UP and Running 👇

kali > hciconfig –help get the commands available to use. Here I am using few commands as an example. Here I use -a, p scan, and name command for example purpose. You can use the man hciconfig command to get more information about hciconfig☺️
🚀 HCITOOL
HCITOOL is another built-in tool of Kali Linux for configuring and finding nearby Bluetooth devices. This tool sends a special command to Bluetooth devices. If no command passed hcitool prints some basic device information and exists🤪
kali > hcitool scan
kali > man hcitoolYou can use the man command to find more information on hcitool. Here I am using some extra commands but you can explore more with practice😝

The scan command will give you a list of the active devices nearby. Here I am using the name, info, and inquiry commands for illustration and just to be extra😝
🚀 SDPTool

Sdptool provides an interface for Bluetooth devices to perform SDP queries and manage a local SDP database.You can use sdptool to get more information on the target device. Use man command to get more information about sdptool.
kali > man sdptool 
🚀 Bt Scanner
Bt scanner is a tool that is specifically designed to collect as much information from a Bluetooth device as possible without the mandatory pairing. A detailed information screen extracts HCI and SDP information and maintains an open link to track the RSSI and connection quality. To get more information use the man command.
kali > man bt scannerThe default screen of the Bt scanner 👇

By pressing the keys given at the end of the page you can run the scans that are available and so various other things. Here I am using an inquiry scan👇

When you’ll press i you’ll get the list of active devices nearby. By clicking on them you can get a lot of information about the device🤭. By gathering as much information as possible it is possible to take an educated guess about the device 👇

🚀 Bettercap

Bettercap includes attack modules😈 for various radio and network technology. only concentrating on the Bluetooth module today, but Bettercap has a lot more to it than just Bluetooth hacking. It is also my personal favourite bluetooth exploit tool -- ☺️
You can download bettercap here 😋
Ultimately, even though it changes its MAC address, we can write data😈 to the target or victim to attempt to exploit ☠️ it, like a tag to monitor the device over time.
After installing bettercap use –help command to know the active modules 👇

To Start searching for Bluetooth devices or list of active Bluetooth devices, type👇
>> net. recon on 
Start bettercap in sniffing mode type👇
>> ble. recon The list of devices that you have discovered from scanning with the command👇
>> ble. show 
After getting the scan results you can dig a little deeper into the device. But the important thing is to know the MAC Address of the target🤠
To enumerate details about the device you can use the command👇
>> ble.enum 🚀 Exploiting the target
You can see that some of the services has write property enabled on them😋 You can access the property. Let's try writing some data on the target device. We can write the value of "any-value-you-want" to that device by typing the command ble.write TheMacAddress TheFieldToWriteTo ValueToWrite. It’s not necessary💩 that you will be able to write on the device all the time, just about 3 out of 5🥸

We can use Bettercap to start poking🤠 around for ways to further exploit nearby devices if we learn a device is running a service with a vulnerability that we can exploit by writing to a value 😏 Using MAC address randomization, we can also use these fields to fingerprint devices, as the values will uniquely identify a device that alters other properties such as its MAC address to try to avoid correlation. Bluetooth radio transmissions can be discovered and unmasked to track the people and devices😈
🚀Conclusion 🤖
Subscribe to receive notifications of similar posts 😜 where we will be reverse engineering malware, vulnerabilities as well as hacking tools, vectors, stories, tutorials and other Infosec stuff...😋
Follow me on twitter for daily Infosec Memes and shenanigans😝
Morans😈

Thank you for taking time and hope you learned something new, Like/Share and leave a comment and as always, stay awesome! 😋👊 💪




Comments