GOOGLE HACKING 🥷
- alvin gitonga
- Jul 26, 2022
- 4 min read
Welcome back Cyber Warriors!

In the last one, we used SHODAN to identify devices in the internet of things (IOT). In this installment, I will show you how touse google to further your recon and OSINT skills in preparation for a pentest. So, Cyber Morans, lets DO THIS! 💪

Google Hacking
Google Dorking or Google hacking refers to using Google search 🔎 techniques to hack into vulnerable sites or search for information that is not available in public search results.
The Google search engine works similarly to an interpreter using search strings and operators. For example, you can say that Google reacts sensitively to certain search strings when applied with specific operators. However, you will learn more about it later in the tutorial on ‘what is Google Dorking’.

Google Hacking, commonly refered to as google dorking is the art of using specific advanced queries in the search to reveal information otherwise shouldnt be available.
Believe it or not, Google Dorks can uncover great information such as email addresses and lists, login credentials, sensitive files, website vulnerabilities, and even financial information (e.g., Payment card data) - And the wonderful thing is that this is an incredibly passive form of attack that doesn’t draw much attention to the hacker. Unfortunately, some people use these techniques for illicit and nefarious activities such as cyberwarfare, digital terrorism, identity theft, and many other undesirable activities.

Google Dorking is not hacking itself. Google Dorking is a technique that comes in handy in one of the phases of hacking, i.e., Information Gathering, and this is the most important phase of hacking. There are five phases of hacking, i.e., reconnaissance, scanning, gaining access, maintaining access, and clearing tracks. Google Dorking is used in the starting phases where hackers try to get all the information linked to any specific organization or an individual. After getting all information then hackers pick out the information they need for the next phases.
PS: You will need to enter a captcha almost every time you use a dork. This way, Google stops bots from using google for illegal purposes.
Google Dorks Operators 🕵️
intitle – This allows a hacker to search for pages with specific text in their HTML title. So intitle: “login page” will help a hacker scour the web for login pages.
allintitle – Similar to the previous operator, but only returns results for pages that meet all of the keyword criteria.
inurl – Allows a hacker to search for pages based on the text contained in the URL (i.e., “login.php”).
allinurl – Similar to the previous operator, but only returns matches for URLs that meet all the matching criteria.
filetype – Helps a hacker narrow down search results to specific files such as PHP, PDF, or TXT file types.
ext – Very similar to filetype, but this looks for files based on their file extension.
intext – This operator searches the entire content of a given page for keywords supplied by the hacker.
allintext – Similar to the previous operator but requires a page to match all of the given keywords.
site – Limits the scope of a query to a single website.
Dorking Syntax
Lets try these operators and queries and get some sensitive and juicy information....No?

Exposed FTP servers: Since File transfer protocols may also contain certain sensitive information and they are not normally meant to be exposed
type "Intitle: index of inurl: ftp" in the google search and Hit Enter! 👇

Clicking on one of these results lands you right inside a FTP server and are staring at the files in the server and able to access, read and write, WITH NO CREDENTIALS whatsoever! 🤭
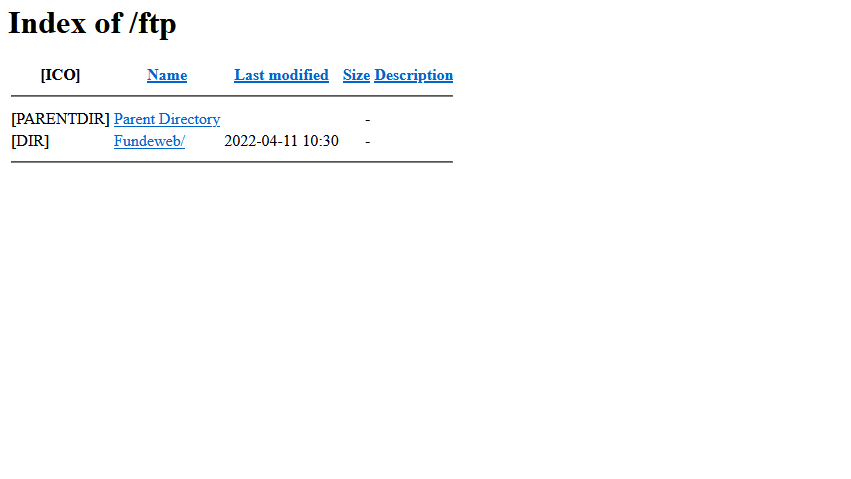
and there are 10 pages of such results...😲

Exposed Webcams and Camera feeds: By applying this search string, you can access open/public webcams or CCTVs available on the internet.
type intitle:”webcamXP 5” and hit search!

clicking on the results gives you a POV of the camera and an adjustable image (zoom in, different angles...etc) here we see a street veiw LIVE. 😲

and here we are in an Office complex and access to both cameras. Veeeery many laptops and desktops....🤭


Filetype(Logs, csv, PDF...)
type filetype:log and hit search! 👇
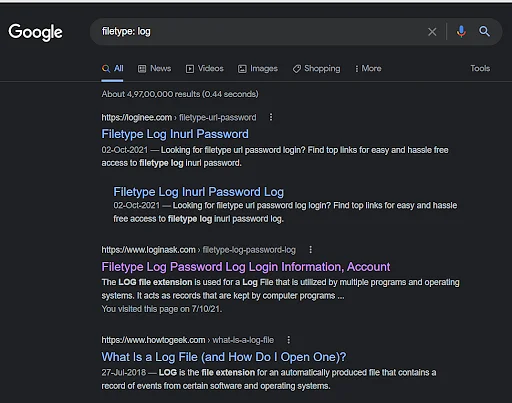
Admin Logins
type inurl admin login.php and hit search! 👇

Usernames and passwords
type allintext:username,password filetype:log and hit search! 👇

other stuff you can find with google dorks 🤌:
💀 Exposed Databases with no/default credentials
💀 SSH keys
💀 Vulnerable servers and systems
💀 SCADA ICS systems
💀 Hidden sites and subdomains and Emails
for more google hacks Click here. This is the Google Hacking Database (GHDB) and contains all hacks/dorks found so far. Go have fun cyber Morans.
Safety Measures Against Google Dorking

You need a good DEFENSE against this dorks;
With the information mentioned in this tutorial on what is Google Dorking, you have understood that your data is not entirely safe on the internet.
To safeguard our information from Google Dorking/Google Hacking to a certain extent, you can refer to some of the below-mentioned measures:
Use passwords to protect data and information directories.
Apply tools to search for loopholes in the information available on the internet.
Store sensitive data and passwords in complex patterns rather than plaintext.
Conclusion
In this tutorial on what is Google Dorking, you understood how to apply Google search techniques to access sensitive information that was knowingly or unknowingly released on the internet. You can also apply advanced search strings to search for important data. For example, Google Dorking is just a way for you to gain experience with the hacking techniques and not perform illegal hacking attempts.
Thank you for your time, Like and leave a comment/review and as always, stay awesome! 👊 💪





Comments